
Bridgestone vs. the Algorithm: A Battle for Control
On September 2, 2025, Bridgestone Americas confirmed it was investigating a “limited cyber incident” that disrupted operations at multiple manufacturing facilities across North America. The affected sites included plants in Aiken County, South Carolina, and Joliette, Quebec, both of which experienced abrupt production halts and internal system outages.
While the company emphasized that no customer data or external interfaces were compromised, the nature of the disruption bore the hallmarks of a ransomware attack—rapid operational impact, lack of immediate attribution, and a focus on operational technology (OT) environments. No threat actor has claimed responsibility, and no ransom demand has been publicly disclosed, but cybersecurity analysts caution that attribution may emerge in the coming weeks.
Bridgestone’s response was swift. According to its public statement, containment protocols were activated immediately, and forensic analysis began to assess the scope of the breach. The company’s IT and cybersecurity teams worked around the clock to minimize supply chain fallout and restore production.
This incident is not Bridgestone’s first brush with ransomware. In 2022, the company was targeted by the LockBit group, which exfiltrated and leaked sensitive data online. The recurrence of cyber threats underscores the growing vulnerability of industrial manufacturers, particularly those with complex OT systems and global supply chains.

As noted by CyberNews, the timing of the Bridgestone breach coincided with a separate attack on Jaguar Land Rover, attributed to the Scattered LAPSUS$ Hunters—a coalition of ransomware gangs including Scattered Spider, LAPSUS$, and ShinyHunters. While no direct link has been established, the parallel disruptions suggest a coordinated campaign targeting automotive and manufacturing sectors.
This article series will explore:
The technical anatomy of the Bridgestone breach
The company’s incident response and containment strategy
Broader implications for OT security in manufacturing
Lessons for cybersecurity professionals navigating hybrid IT/OT environments
In an era where ransomware actors increasingly target uptime over data, Bridgestone’s experience serves as a stark reminder: the battle for control is no longer theoretical—it’s operational.
Timeline of a Digital Disruption
In early September 2025, Bridgestone Americas experienced a cyber incident that disrupted operations at multiple manufacturing facilities across North America. While the company has not publicly confirmed ransomware involvement, the nature and scope of the disruption strongly suggest a targeted intrusion into its operational technology (OT) infrastructure. Below is a reconstructed timeline based on publicly available information and industry-standard incident response patterns.
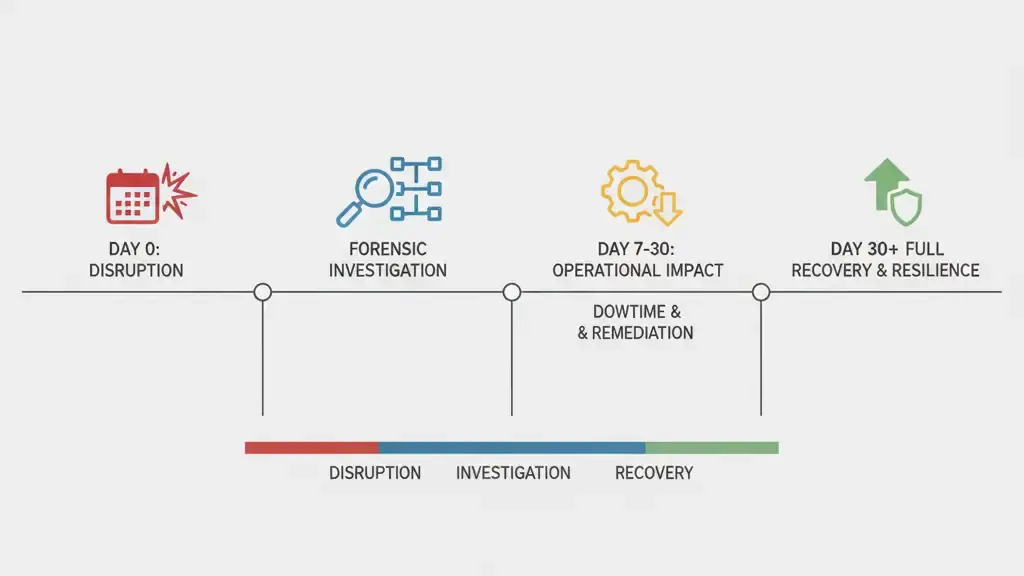
Timeline of Events
September 2, 2025 — Initial Disruption at Aiken County, SC
Bridgestone’s facility in Aiken County, South Carolina, reported unexplained system outages and halted production lines. The company initiated containment protocols and launched an internal investigation. Public disclosure was limited to a brief statement describing a “cyber incident” affecting “some manufacturing facilities” (BleepingComputer).
September 3, 2025 — Joliette Facility Impacted
Similar disruptions were reported at Bridgestone’s Joliette, Quebec plant, one of its largest Canadian facilities. Local media noted operational shutdowns and IT system failures. Bridgestone expanded its forensic analysis and confirmed the issue was not isolated. No external systems or customer data were reported compromised.
September 4–5, 2025 — Containment and Escalation
Bridgestone publicly stated that its team “responded quickly to contain the issue in keeping with our established protocols.” The company did not confirm ransomware involvement, but cybersecurity analysts noted the hallmarks of such an attack: rapid propagation, OT disruption, and lack of immediate attribution. No threat actor claimed responsibility, and no ransom demand was disclosed (CyberNews).
September 6–10, 2025 — Forensic Investigation and Sector Alerts
Bridgestone continued its forensic investigation to determine the root cause and scope of the breach. The timing of the incident coincided with a separate cyberattack on Jaguar Land Rover, attributed to the Scattered LAPSUS$ Hunters—a coalition of ransomware groups including Scattered Spider, LAPSUS$, and ShinyHunters. While no direct link has been established, the parallel disruptions suggest a possible coordinated campaign targeting automotive and manufacturing sectors.
September 11–14, 2025 — Operational Restoration and Strategic Review
Bridgestone began phased restoration of affected systems. Internal audits and external consultations were launched to assess vulnerabilities and reinforce OT segmentation. No further disruptions were reported, though full recovery timelines remain undisclosed.
Inferred Details
Ransomware Likelihood: While Bridgestone has not confirmed ransomware, the operational impact and containment strategy are consistent with ransomware behavior. This inference is based on prior incidents, including the 2022 LockBit attack on Bridgestone (SecurityWeek).
Targeting of OT Systems: The disruption of manufacturing lines without evidence of data exfiltration suggests attackers may have targeted OT systems or supervisory control interfaces. This is a growing trend in ransomware campaigns against industrial firms.
Threat Actor Attribution: No group has claimed responsibility. The overlap with the Jaguar Land Rover breach may indicate shared tactics or infrastructure, but attribution remains speculative.
Measuring the Fallout
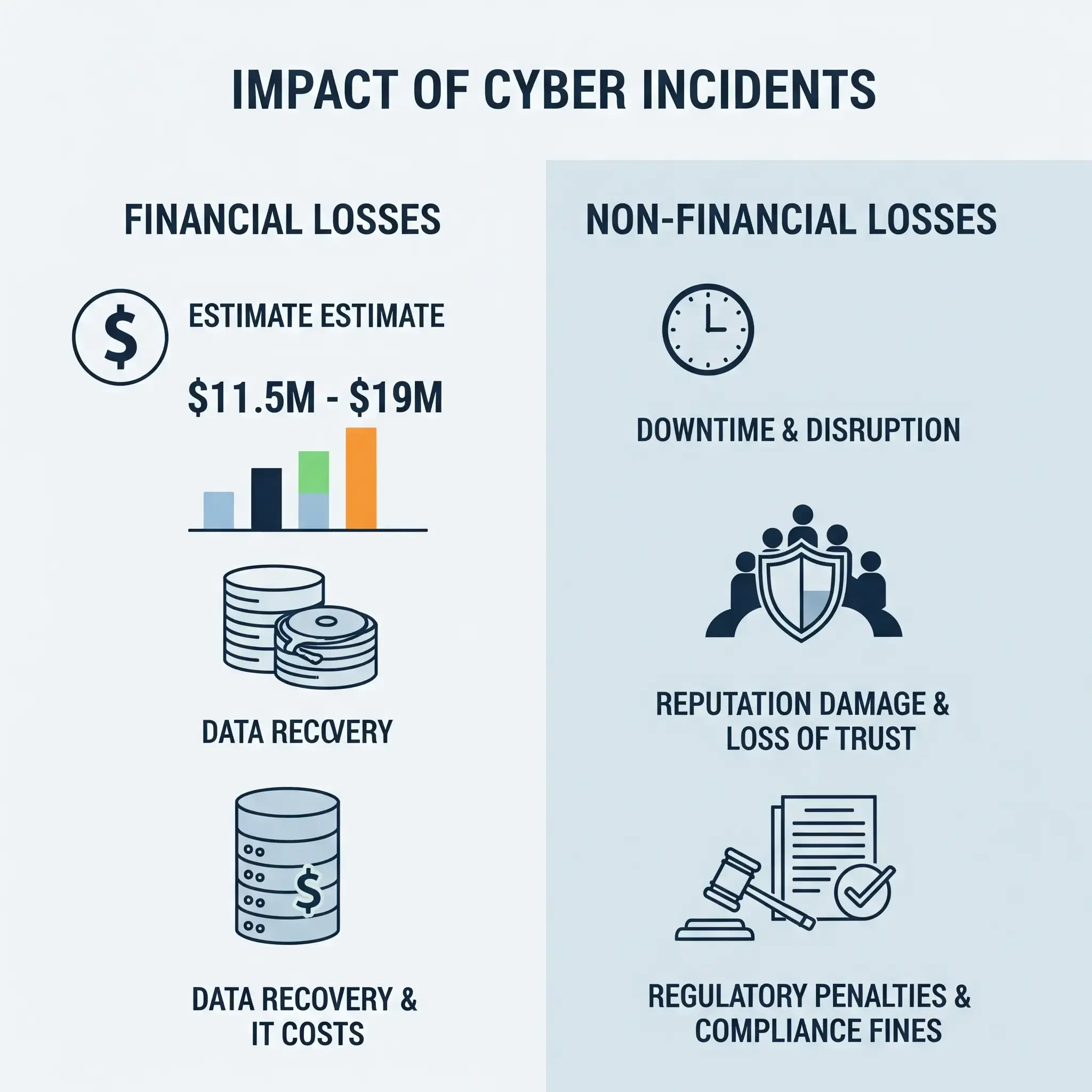
The cyberattack on Bridgestone Americas in early September 2025 disrupted operations at key manufacturing facilities in Aiken County, South Carolina, and Joliette, Quebec. While the company has not disclosed specific financial losses, the scale and nature of the disruption allow for a grounded estimation of its impact. This section outlines both direct financial costs and broader strategic consequences.
Financial Losses
1. Production Downtime
Bridgestone’s facilities produce tens of thousands of tires per day. The Joliette plant alone has a capacity exceeding 20,000 tires daily.
Estimated revenue loss per day: $2–3 million per facility
Duration of disruption: 2–3 days
Total estimated production loss: $8 million–$12 million
2. Labor Costs and Idle Time
Employees were offered the option to perform preventive maintenance or go home without pay.
Estimated cost in wages and lost productivity: $500,000–$1 million
3. Incident Response and Forensics
Bridgestone mobilized internal teams and likely engaged external cybersecurity consultants.
Estimated cost of containment, investigation, and recovery: $1 million–$2 million
This includes forensic analysis, system restoration, and post-incident audits.
4. Supply Chain Disruption
Delayed shipments to OEMs and distributors may result in contractual penalties and lost sales.
Estimated downstream impact: $2 million–$4 million
This figure accounts for ripple effects across North American logistics and retail channels.
Non-Financial Losses
1. Operational Disruption
The attack halted production lines and disrupted internal systems, requiring full system isolation and phased restoration. Restarting OT environments is complex and time-consuming.
2. Reputational Damage
This is Bridgestone’s second major cyber incident in recent years, following the 2022 LockBit ransomware attack. Repeated breaches may raise concerns among partners, regulators, and investors.
3. Strategic Exposure
The incident highlights vulnerabilities in Bridgestone’s OT infrastructure. It underscores the need for improved segmentation, access controls, and real-time threat detection.
4. Regulatory Scrutiny
While no customer data was compromised, Bridgestone may face inquiries from U.S. and Canadian regulators regarding its cybersecurity posture and incident response protocols.
Estimated Total Impact
| Category | Estimated Loss (USD) |
|---|---|
| Production Downtime | $8M–$12M |
| Labor and Idle Time | $0.5M–$1M |
| Incident Response & Forensics | $1M–$2M |
| Supply Chain Disruption | $2M–$4M |
| Total Estimated Financial Loss | $11.5M–$19M |
This estimate does not include long-term reputational damage, regulatory costs, or strategic remediation efforts, which could push the total impact higher over time.
Building Resilience with Cy-Napea®’s Six-Layer Defense
The September 2025 cyberattack on Bridgestone Americas disrupted operations at two major manufacturing facilities and exposed the vulnerabilities that industrial enterprises face when IT and OT systems converge. While Bridgestone managed to contain the breach and resume operations, the incident underscores the need for a comprehensive, layered cybersecurity strategy.
Cy-Napea®’s Cyber Cloud platform offers a six-layer defense architecture designed to prevent, detect, and recover from sophisticated threats. Each layer plays a critical role in protecting infrastructure from ransomware and operational sabotage.
1. Security Awareness Training
Cy-Napea®’s Cybersecurity Awareness Training transforms compliance into culture.
Monthly video updates, phishing simulations, and gamified learning modules help employees recognize threats and respond appropriately.
A multi-tenant dashboard enables administrators to manage campaigns and track engagement across teams.
2. Email Security

Cy-Napea®’s Email Security module provides comprehensive protection against phishing, malware, and impersonation attacks.
MX-Based Deployment: Email traffic is routed through Cy-Napea®’s secure filtering infrastructure via MX record redirection, allowing full inspection and policy enforcement without requiring changes to user mail clients.
Microsoft 365 and Google Workspace Integration: Seamless compatibility via journaling or API, supporting hybrid environments and centralized policy management.
Retention and Archiving Policies: Enables email retention for legal and regulatory purposes, including eDiscovery and legal hold functionality.
Centralized Management and Reporting: Administrators can manage policies, monitor events, and generate compliance reports from a single console.
Additional features include URL filtering, attachment sandboxing, and account takeover detection.
3. Endpoint Detection and Response (EDR/XDR)
Cy-Napea® provides both EDR and XDR capabilities.
EDR offers real-time telemetry, attack chain visualization, and endpoint isolation.
XDR expands visibility across networks, cloud workloads, and applications, enabling coordinated response and automated remediation.
4. Backup and Restore
Cy-Napea®’s Backup and Advanced Backup modules ensure data integrity and rapid recovery.
Features include full image backup, granular file recovery, AES-256 encryption, and boot testing.
These tools enable organizations to recover quickly from ransomware without paying a ransom.
5. Disaster Recovery
The Disaster Recovery module provides instant failover to cloud infrastructure, ensuring business continuity.
Supports 20+ workload types across Windows, Linux, VMware, and Microsoft 365.
Automated orchestration and incremental failback reduce downtime and simplify recovery.
Multi-cloud recovery options include Cy-Napea® Cloud, Microsoft Azure, and hybrid configurations.
6. Remote Monitoring & Management (RMM)
Cy-Napea®’s RMM module delivers proactive oversight and intelligent automation across endpoints and infrastructure.
Device Health Monitoring: Tracks CPU, memory, disk usage, and system status to identify performance issues or anomalies.
Remote Access & Troubleshooting: Provides secure remote access for IT administrators to investigate and resolve issues without physical presence.
Patch Deployment: Supports remote installation of OS and application updates to maintain security and performance.
Software Inventory & Usage Tracking: Maintains visibility into installed applications and usage patterns to support license management and compliance.
Alerting & Reporting: Generates real-time alerts and periodic reports on system health, security events, and update status.
Final Reflection
Bridgestone’s experience is a stark reminder that resilience is not built on firewalls alone. It requires a multi-layered strategy that spans human behavior, endpoint intelligence, cloud recovery, and real-time oversight. Cy-Napea®’s six-layer defense model offers a blueprint for industrial organizations seeking to protect uptime, reputation, and operational integrity in an era of algorithmic threats.




